Fake Mobile Phone Towers Are Controlling Your Mobile – Blame The Lincolnshire Poacher
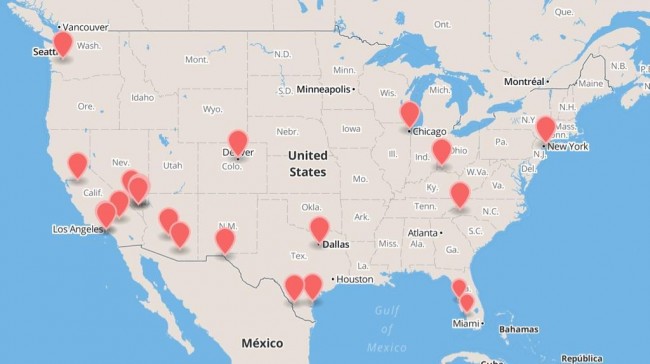
ARE fake mobile phone towers controlling your mobile phones? Popular Science count at least 17 fake mobile phone towers across the United States.
Like many of the ultra-secure phones that have come to market in the wake of Edward Snowden’s leaks, the CryptoPhone 500, which is marketed in the U.S. by ESD America and built on top of an unassuming Samsung Galaxy SIII body, features high-powered encryption. Les Goldsmith, the CEO of ESD America, says the phone also runs a customized or “hardened” version of Android that removes 468 vulnerabilities that his engineering team team found in the stock installation of the OS.
His mobile security team also found that the version of the Android OS that comes standard on the Samsung Galaxy SIII leaks data to parts unknown 80-90 times every hour. That doesn’t necessarily mean that the phone has been hacked, Goldmsith says, but the user can’t know whether the data is beaming out from a particular app, the OS, or an illicit piece of spyware. His clients want real security and control over their device, and have the money to pay for it.
To show what the CryptoPhone can do that less expensive competitors cannot, he points me to a map that he and his customers have created, indicating 17 different phony cell towers known as “interceptors,” detected by the CryptoPhone 500 around the United States during the month of July alone. (The map below is from August.) Interceptors look to a typical phone like an ordinary tower. Once the phone connects with the interceptor, a variety of “over-the-air” attacks become possible, from eavesdropping on calls and texts to pushing spyware to the device.
“Interceptor use in the U.S. is much higher than people had anticipated,” Goldsmith says. “One of our customers took a road trip from Florida to North Carolina and he found 8 different interceptors on that trip. We even found one at South Point Casino in Las Vegas.”
Who is running these interceptors and what are they doing with the calls? Goldsmith says we can’t be sure, but he has his suspicions.
“What we find suspicious is that a lot of these interceptors are right on top of U.S. military bases. So we begin to wonder – are some of them U.S. government interceptors? Or are some of them Chinese interceptors?” says Goldsmith. “Whose interceptor is it? Who are they, that’s listening to calls around military bases? Is it just the U.S. military, or are they foreign governments doing it? The point is: we don’t really know whose they are.”
Who needs the information? And why?
Meanwhile…in England the Lincolnshire Poacher plays on. Do listen to this – it’s brillaint:
Posted: 4th, September 2014 | In: Reviews Comments (3) | TrackBack | Permalink


